I have two UniFi USGs, each on its own local controller, and I wanted to set up a site-to-site IPsec VPN. Here’s what worked.
From my research, you can’t use Auto configuration when you have two controllers, so I used manual, mostly following advice in this thread.
IPsec only allows entering IP addresses, not hostnames, so if the IP addresses are dynamic and they change, you’ll need to update both sides again.
In my scenario:
- Sites A and B each have their own subnet.
- Sites A and B have public IPs visible to the USGs. No double-NAT involved.
- Site A needs to be able to access Site B but not vice-versa, so we need to look at the firewall as well.
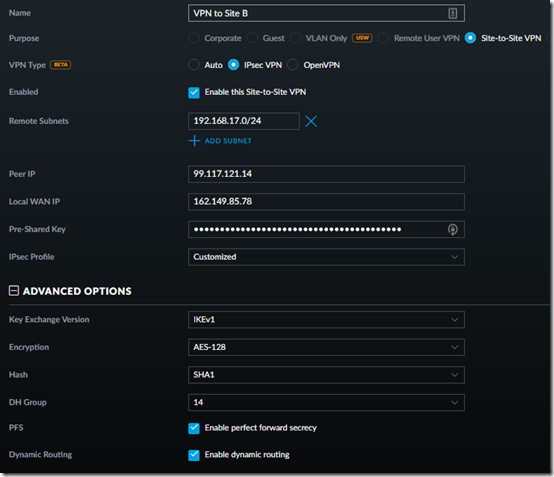
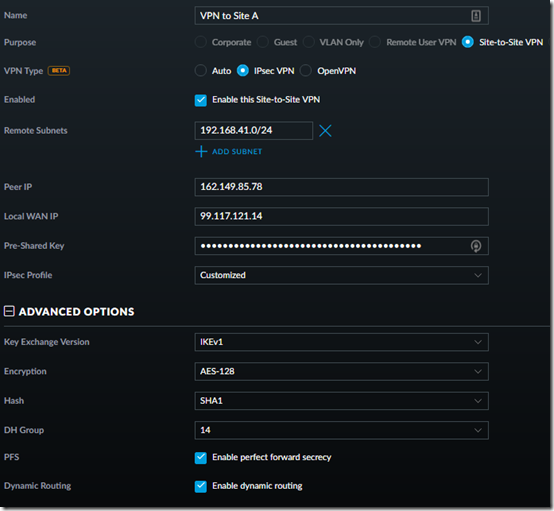
1. Set up the VPN at Site A, using Site B’s subnet and the public IP addresses of Site A and Site B, respectively, I used a password generator to create a 40-character Pre-Shared Key:
2. Set up the VPN at Site B, using Site A’s subnet, the public IP addresses of Site B and Site A, and the same Pre-Shared Key. (Note: if the other side will be an EdgeOS device like an ER-X instead of a USG, turn off Dynamic Routing. See this post.)
3. Both sites already have firewall rules that block communication among private subnets (used for VLANs). See this post to set that up.
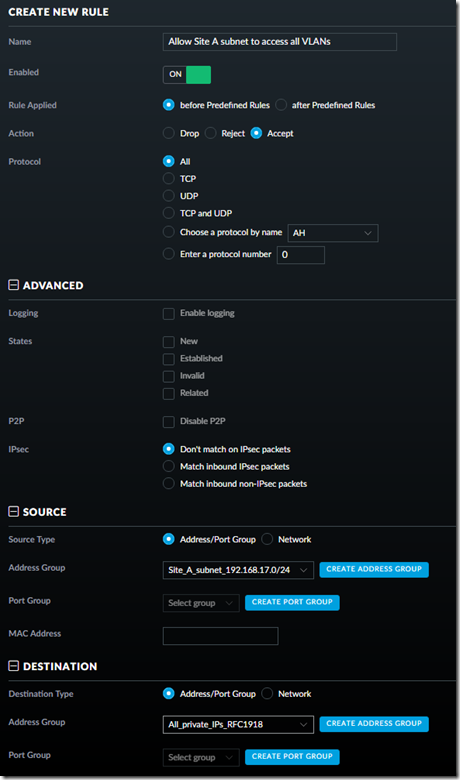
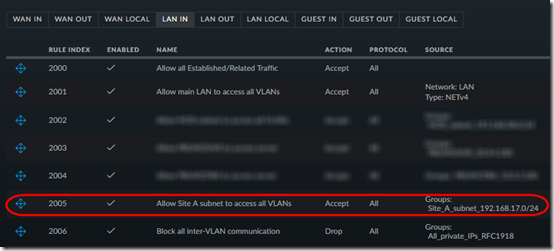
To allow Site A to access Site B, we need a new rule at Site B that creates an exception for packets coming from Site A’s subnet. Create a firewall Address Group for Site A’s subnet, then add this rule in LAN IN:
After creating the LAN IN rule, move it above the rule that blocks inter-VLAN communication:
4. Once both USGs have finished provisioning, you should now be able to ping from Site A to a pingable host behind Site B.
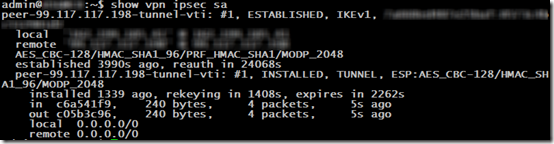
5. The dashboard will report that the VPN is down, but it’s not:

To check the VPN status, SSH into one USG and type show vpn ipsec sa:

Hi, thanks for your write up, when I tried it all I get is the following. Any idea?
@ubnt:~$ show vpn ipsec sa
(unnamed): #44, CONNECTING, IKEv1, bea5caedda75e526:516b03af439bbb03
local ‘%any’ @ xxx.xxx.xxx.xxx
remote ‘%any’ @ xxx.xxx.xxx.xxx
AES_CBC-128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048
passive: ISAKMP_VENDOR MAIN_MODE
Mike, did you trying pinging from a device behind the first USG to a device behind the second USG? Not sure if it’s true for USG, but in general, sometimes you have to ping (or otherwise access the remote network) to get the tunnel to start.
Also, are you using the string “%any” somewhere? I hard-coded the IP addresses in Peer IP, and they appear both before and after the @ sign in the show vpn output. Let me know if you get “%any” to work and how.
Hi Mark, thanks for getting back to me. So I ran sudo swanctl –log and saw 13[ENC] invalid ID_V1 payload length, decryption failed?
I Verified the keys were the same….so for giggles I recreated my preshared keys with longer keys and for whatever reason, it worked and I pinged through.
¯\_(ツ)_/¯
https://www.reddit.com/r/Ubiquiti/comments/8wo64t/2_cloud_keys_site_to_site_vpn_fail/
Good to hear! So what’s with the “%any”? Did you figure out how to get it to work behind dynamic IPs?
I honestly dont know why it returns %any, it was in the output. I have the ip’s hard coded too. To my knowledge you can’t really use any type of dynamic dns so I will just have to keep an eye on the ip’s and take it as “acceptable risk” though they ip’s don’t really change much, I do have my own dydns server so I will always able to “locate” them should they change. What firmware version are you running? I wonder if %any is a function of latest and greatest firmware.
Firmware is 4.4.22. I thought I’d seen threads about how to use dynamic IP (yeah it would have to be with a DynDNS type address) but I’m doing the same as you: hard-code and when it rarely breaks, scratch my head until I remember I need to update the IP.
Greetings Sir! the same with Sir Mike the status of the vpn is connecting, I even added some characters for the presharedkey just to make it longer and also the ‘%any’.
I’m using both usg: usg4p and usg3p .
The usg3p has a static wan IP while the usg4p is PPPoe behind a bridge mode modem.
Thank you in advance sir!
Roselyn – sorry but pretty much everything I know is in the article. On my system, “show vpn ipsec sa” still does not return “%any @”. I would suggest contacting UniFi support via chat.