You have a UniFi Security Gateway (USG). You want to allow your LAN to talk to all VLANs, but VLANs cannot talk to the LAN or to other VLANs. How do you configure the USG firewall?
First: define your networks as Corporate. I tried adding firewall exceptions to a Guest network and never got it to work.
This article and this thread contain helpful tips, especially the bits about allowing established/related traffic.
All rules are defined on LAN IN.
1. Add a LAN IN rule to “Allow all Established/Related Traffic”:
Action: Accept
Protocol: All
States checked: Establish, Related <—don’t miss this step!
Source: leave blank
Destination: leave blank
As UBNT-jaffe says here, “Adding this rule at the top will allow all established and related stateful firewall traffic to be able to pass (basically all ‘reply’ traffic).”
2. Add a group “All_private_IPs_RFC1918”:
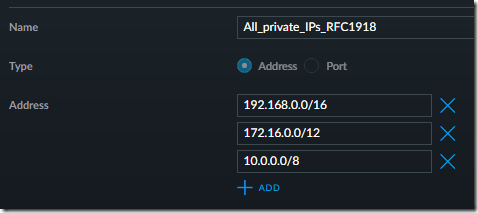
This allows us to target all private subnets (those that do not route to the Internet).
3. Add a LAN IN rule to “Allow main LAN to access all VLANs”:
Action: Accept
Protocol: All
States checked: none (applies to all states)
Source: Network – LAN (NETv4)
Destination: Address/Port Group “All_private_IPs_RFC1918”
This serves as the exception to the next rule.
4. Add a LAN IN rule to “Block all inter-VLAN communication”:
Action: Drop
Protocol: All
States checked: none (applies to all states)
Source: Network – Address/Port Group “All_private_IPs_RFC1918”
Destination: Address/Port Group “All_private_IPs_RFC1918”
Note At first glance, you might think that this rule would block communication within each subnet as well, for example blocking 10.5.2.15 from talking to 10.5.2.72. However, that “Layer 2” traffic is handled in your switch(es) and never touches the USG, so the rule has no effect there. Only inter-subnet traffic comes back up to the “Layer 3” routing in the USG.
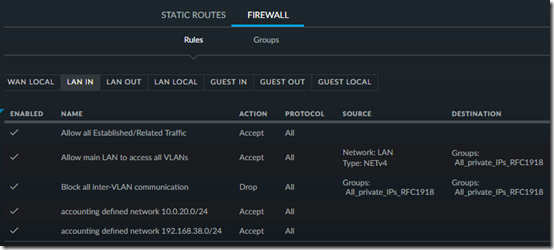
At this point, your rules will look like this:
Bonus Tip
Now, what if you have one device on a VLAN that needs access to one device on the LAN, maybe a laptop that must send backups to a server?
a. Create “Device1” and “Device2” groups. Even though they are “groups,” put just one IP address in each group.
b. Add this rule then move it above the “Block all inter-VLAN communication” rule created in step 4 above:
Action: Accept
Protocol: All
States checked: none (applies to all states)
Source: Network – Address/Port Group “Device1”
Destination: Network – Address/Port Group “Device2”

This is helpful! Thanks for posting this. This opens my eyes to a better way of organizing my firewall rules for VLAN communication instead of a blanket block, or a blanket allow.
I think I have a pretty good handle on the different settings in the firewall, except for the connection type. I really don’t know the difference between established, new, related, etc. That part confuses me, and I’m sure I would make better rules if I understood them fully.
I’ve also seen a lot of questions on the nets about WAN In, LAN In, WAN out, LAN out and Local…. I found a few places on the interwebs that helped me break it down, and understand it, but that took hours of research to piece it all together. It may help to describe this as well.
It is confusing. The comment by UBNT-Jaffe here shed a little light on established/related:
https://community.ubnt.com/t5/UniFi-Routing-Switching/USG-Pro-Disable-Inter-Vlan-routing/m-p/1987567/highlight/true#M50138
Finally! Thanks for the help in getting my LAN to talk to my VLAN. New to using Unifi gear and this was my only issue thus far.
This could be the “holy grail” of UniFi firewall posts. Thanks for this!
Mark,
Thanks for this. I followed your guide and added a rule to allow all private IPs access my Airplay speaker. It seems to only work when I allow the airplay speaker “new” access rather than only established/related. Any idea why I have to give it “new” access?
JC – I don’t know your topology but my understanding is that “established/related” allows _reply_ traffic whereas “new” would be for traffic that is _initiated_ at the specified Source. In step 3 of the article, I say to leave all States unchecked, which should mean allow all states.
I would NEVER put this rule below. This is because, in case of being compromised, the 1st. network which will be compromised will be the gateway network from WAN – which in this case is LAN. Effectively, by having this rule, it allows the attacker to subsequently compromise the entire system. Defeating the very purpose of having managed switches / VLAN tagging.
In fact, the standard practice is NOT to have ANY device in LAN or default network.
Add a LAN IN rule to “Allow main LAN to access all VLANs”:
Action: Accept
Protocol: All
States checked: none (applies to all states)
Source: Network – LAN (NETv4)
Destination: Address/Port Group “All_private_IPs_RFC1918”
@BM, thanks for that perspective. My main reason for VLAN tagging is to keep the phones, cameras, and especially the guest computers on Wi-Fi away from the main LAN. I see the threat from rogue devices inside the network as greater than the threat from outside. If an attacker can compromise the firewall from outside and get access to the LAN, I’ve got bigger things to worry about than whether they can also access a phone or camera.
“In fact, the standard practice is NOT to have ANY device in LAN or default network.” I assume you mean that everything is on a VLAN? I’d be interested to see an article explaining this “standard practice”–it’s not something I’ve encountered in the small-business space.
This was a great straight-forward tutorial with perfect explanations of the steps. I followed a few other guides and was getting some weird unexplainable (at least to me) behavior when I tested it.
This worked perfectly and I understand whats happening.
I thought I’d drop by the comments here to express my gratitude.
Everything else I’d found online suggested that I should be able to route from a UniFi Corporate LAN to my Guest VLAN hosted IoT devices (eg. AV Receiver/Spotify Connect, Apple TV etc).
I wasted an untold number of hours trying to get things to work; messing with mDNS and IGMP and various firewall settings. I finally found and followed your advice by changing the IoT VLAN to a corporate network with appropriate firewall rules. Now everything’s golden.
You’re a star.
Dave, glad it helped. I feel your pain. So frustrating when what seems obvious (putting guest devices on a Guest network) doesn’t work! Maybe there’s a way, but at least the communication among Corporate VLANs is comprehensible.
Hi.
I have read several guides for setting firewall rules in the Unifi USG.
And i Source/Destination. Some say to use Groups as you have used, but some use
And some say to use Groups as you do, and some say to use “Network”.
What is the main differance between using groups and network in the source/destination?
Regards
Extermini
Extermini, as you can see, I use both:
Source: Network – LAN (NETv4)
Destination: Address/Port Group “All_private_IPs_RFC1918”
The Network is one specific network as defined in the router (one subnet).
The group covers multiple subnets.
So maybe if you are targeting one subnet, use the name of that network. If you want to target multiple subnets in the same rule, use a group.
Hi.
Thanks for the quick explantion.
In the newer version of Unifi controller. The Source: “Network” you can choose between IPV4 subnet and USG ip adress. What is the differance and what to use?
Regards
Extermini
Extermini – I’ve only used “IPv4 Subnet”. If it had to guess, I would assume that “USG IP Address” refers specifically to the single IP address of the USG itself. I guess that could be used if you want to allow some traffic (like ICMP for ping) to reach the USG but not go anywhere else.
Hey Mark, great and to the point information without any BS surrounding it. I like it. One question; i also have this page in my bookmarks: https://www.missingremote.com/guide/2018/08/configure-unifi-to-block-access-from-one-iot-vlan-to-all-vlans
I think 1 and 2 over there correspond with 1 and 2+3 over here; then the only difference is that the other site blocks IoT to main VLAN where you block all inter-VLAN communication by default, right?
Additional question regarding getting Sonos on my IoT VLAN:
Do you perhaps also know if I still have to do stuff for accessing Sonos on my IoT network from my main LAN if i follow this guide: https://help.ubnt.com/hc/en-us/articles/360001004034-UniFi-Best-Practices-for-Managing-Chromecast-Google-Home-on-UniFi-Network
I haven’t set that part up but i read some contradicting blogs;
– https://blog.awelswynol.co.uk/2017/11/unifi-sonos-and-vlans
– https://blog.awelswynol.co.uk/2018/04/sonos-unifi-vlan-and-firewalls
– https://durdle.com/2018/12/09/unifi-vlans-sonos-and-igmp-proxy/
Hi Gilles, that’s a bit too detailed to discuss in a blog comment. In most cases, once you understand the principles of opening ports and the hierarchy of rules, with a little trial and error, you’ll get the setup you need. You might want to temporarily put a laptop (with its local firewalls off) on your IoT VLAN so you can test pinging to and from it.
Thanks for this post, Mark! Very insightful
I’m curious – do you still consider the above good practice?
In particular, I’m wondering how the firewall rules you’ve described work with / against features (from more recent Unifi updates) like Port Isolation and “Block LAN to WLAN Multicast and Broadcast Data”.
C
CM – This is not a “best practice” article. It’s about how to address a specific need: let the main VLAN initiate communication with other VLANs but not vice-versa. And yes, I still use it.
I’m not using either of the features you mention. From their names, they serve other purposes. One is about blocking communication _within_ a VLAN; the other about LAN to WLAN.
So, it depends on what you need to do.
Mark,
I’ve followed your guide and it works perfectly. I’ve gotten stuck on setting up a follow up rule however. I have a DNS host on LAN Pi-Hole. Lets say 192.168.1.3 and I have a IoT Vlan 192.168.2.0/24 with some devices on it. I have blocked inter-vlan traffic per your blog but how do I allow IoT device to hit DNS on LAN? I’d really like any of those VLANs to be allowed to hit my dns host on 53.
The IoT vlan gets DNS handed to it via dhcp just fine.
I’ve got a rule in LAN-IN just above the drop all rule.
Something like:
Action: Accept
Protocol: TCP and UDP
States checked: none (applies to all states)
Source: Any
Destination: Address/Port Group > 192.168.1.3/53
In any other firewall I’d already have this sorted out but I’m stumped. Am I doing this right? Thanks!
Robert – sounds right to me. Maybe there is a default rule on another section of the firewall that blocks DNS traffic. If you haven’t already, I’d suggest posting in the Ubiquiti community (https://community.ui.com/questions).
I used this to setup my IoT network and deny access to my main network. Thank you.
Hey Mark!
I followed your steps exactly but cannot access my UnRaid server on my main LAN from my VLAN.
Any ideas?
@Jason, sorry but I’d need a lot more info to troubleshoot your setup. It can be painstaking work to add a rule, wait for it to propagate to the USG, trying pinging the device, and repeat. I’d suggest posting a query in the Ubiquiti community (https://community.ui.com/questions).
All good just curious as I followed your exact details but of course the Groups would have the specific devices I want to communicate to each other. One being a VLAN10 Devices group, which is a TV and my smartphone to test, and the other being a LAN Devices group, which is my Unraid server hosting Plex.
I have posted my whole setup to the community with no responses yet. Guess I shall just wait
Thanks!
Oh and I have been using Putty to SSH into the USG to send the “clear connection-tracking” after allowing Provisioning of the USG to complete after each rule chnage
@Jason, reading your first comment more carefully, it says you can’t access the main LAN from the VLAN? If so, that is exactly as designed. As it says in the second sentence, “You want to allow your LAN to talk to all VLANs, but VLANs cannot talk to the LAN or to other VLANs.”
The principal behind this was, the main LAN is the secure, wired, internal, trusted, virus-protected computer network.
The VLANs are used for less secure “Internet of Things” devices (cameras, phones, TV, Amazon Echo, etc.).
It’s okay for computers on the secure network to get into the IoT devices, but we do NOT want the more vulnerable/hackable/insecure IoT devices getting into the main LAN.
IF there are exceptions, things on the VLAN that need to access the LAN, you need to set up individual rules for them as described under “Bonus Tip.”
Does that help?
Agreed with everything you said above and even though I followed the steps above my main LAN cannot access my VLAN with a PING for example. I should have explained further.
I proceeded with your Bonus Tip section by creating a new rule, making sure to place it above the “Block all inter-VLAN communication” rule, selecting your options listed and created two groups. Source > Address Group ‘VLAN10 Devices’ > Has in two IP addresses of two devices with Plex Client app and Destination > Address Group ‘LAN Devices’ > Has in one IP address of my Unraid server as that is hosting my Plex server.
So all that is really subjected is an attack from those 2 clients in VLAN10 to the 1 client in my main LAN.
Here is a link to the Community thread on UBNT I created with this issue. Perhaps there is details on there I have not explained here.
https://community.ui.com/questions/Communication-between-Main-LAN-and-VLAN/f0d8c12b-c348-4246-ab7f-90c146f977a4
Thanks in advance for your help and the explanations above!
@Jason, your UniFi post mentions ExpressVPN, which I’m not famliar with. Is VPN traffic traversing the Internet? I wonder if you’re need encapsulation (see related post: https://www.mcbsys.com/blog/2018/08/usg-to-usg-vpn-fails-with-att-u-verse/). Can you test it without the VPN?
@Mark, Yes the VPN VLAN is indeed working and traversing internet. I have removed the JSON file just to test and forced a provision of the USG. The VPN stopped working but still no luck with LAN to VLAN communication and vice versa.
@Jason, so the VLAN and LAN are on the same physical switch, no VPN required between them?
I wonder if there is some difference in the way the switch is configured. I use a (Cisco) switch that designates certain ports as belonging to certain VLANs. The devices themselves are not VLAN-aware–they’re “dumb” devices thinking they are just on a regular network. Pretty sure this means that the VLAN tagging is stripped from the packets as they traverse the switch. Really shouldn’t matter, though, as long as your VLAN devices are getting IP addresses on the VLAN…
@Mark, That is correct. The VPN is attached to that VLAN so any devices on that VLAN will use ExpressVPN to gain access to region-blocked content.
Yes which is also possible with Ubiquiti. Just find it odd that I cannot ping something on a VLAN from my main LAN which is the first issue.
So all your instructions above are only to be entered in the LAN IN section? That is all that I have done so assuming it would work but guess I had no luck.
@Jason, yes that’s all LAN IN in this article because all the traffic is on the local network. I do use VPNs but only through USGs. The third-party VPN may be renaming networks, not sure–you may need to get into the command line to tell. I seem to remember an article on the UniFi site about what all the different firewall sections mean. It gets pretty confusing. I think this was it:
https://help.ubnt.com/hc/en-us/articles/115003173168-UniFi-USG-UDM-Introduction-to-Firewall-Rules
Perfect – thank you! I was struggling with this issue and was happy to find your article – worked well for me.
I tried this and it didn’t correct the issue I’m having. I’m trying to access NAS and printers on a VLAN from the LAN. When I run traceroute, the packets are dropped at the gateway of the subnet that the PC is on.
@Jason, click on the last picture in the article to enlarge it. Do your first three LAN IN rules match and are they in that order?