I’m trying to figure out why my new Server 2016 with the Essentials role is getting System events 36874. In particular, if this is a certificate issue between a client and the server, which client are we talking about?
Note the highlighted line in the event’s XML:
Log Name: System
Source: Schannel
Event ID: 36874
User: SYSTEM
Description:
An TLS 1.2 connection request was received from a remote client application, but none of the cipher suites supported by the client application are supported by the server. The TLS connection request has failed.
Event Xml:
<Event xmlns=”http://schemas.microsoft.com/win/2004/08/events/event”>
<System>
<Provider Name=”Schannel” Guid=”{1F678132-5938-4686-9FDC-C8FF68F15C85}” />
<EventID>36874</EventID>
<Version>0</Version>
<Level>2</Level>
<Task>0</Task>
<Opcode>0</Opcode>
<Keywords>0x8000000000000000</Keywords>
<TimeCreated SystemTime=”2017-08-04T08:06:56.497965700Z” />
<Correlation ActivityID=”{88A704FB-0CBC-0001-0F05-A788BC0CD301}” />
<Execution ProcessID=”632″ ThreadID=”11640″ />
<Channel>System</Channel>
<Security UserID=”S-1-5-18″ />
</System>
<EventData>
<Data Name=”Protocol”>TLS 1.2</Data>
</EventData>
</Event>
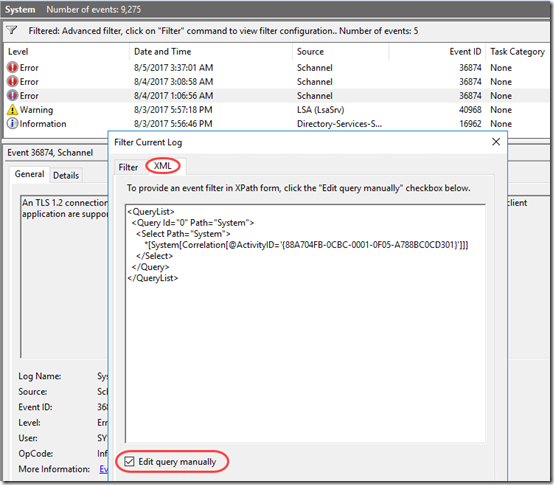
I got the impression from this article that if I found the other events with the same Correlation Activity ID, I might be able to figure out what client is involved. This TechNet article describes filtering the event log using XML filtering. After some tinkering, I came up with this XML filter to identify all System events with the same Correlation ActivityID:
<QueryList>
<Query Id="0" Path="System">
<Select Path="System">
*[System[Correlation[@ActivityID='{88A704FB-0CBC-0001-0F05-A788BC0CD301}']]]
</Select>
</Query>
</QueryList>
And it works: after entering that filter on the XML tab, I see five related events. Still don’t know why I’m getting the TLS error, but now I see from the Information event that it’s possibly related to the Directory Services SAM database. Seems like this event filter might come in handy.