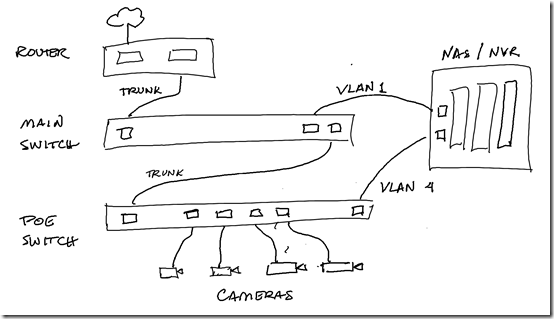
I’ve recently set up a Synology DS1520+ Network Attached Storage (NAS) device at a client site. It’s being used as a Network Video Recorder (NVR) running Synology Surveillance Station, recording 12 cameras. It will also be used for general business backups.
The NAS has four gigabit network ports. At this site, cameras are isolated on VLAN 4. I wanted the camera traffic to be able to go directly to the NAS without crossing VLAN boundaries. I set up one of the NAS’s network interfaces on the main LAN for general use, and connected the second one to the a ports tagged for VLAN 4 traffic:
The switches in use here are Layer 2 switches, so if traffic needs to cross VLAN boundaries, that traffic will need to go up to the router to do the Layer 3 switch. However if the traffic can be kept on the same subnet, it should be able to get the MAC address of the target device with a broadcast query on the same subnet (“Who has 192.168.4.110?”). The MAC is all that is needed for Layer 2 communication.
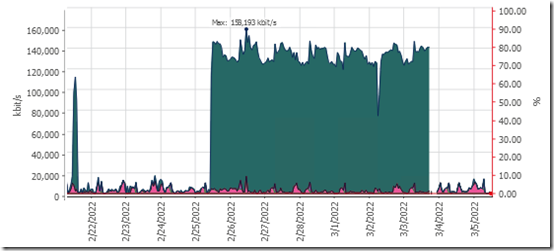
This was working fine when I had a previous NVR that only talked on VLAN 4. However once that was removed, the Synology NAS started talking to the cameras from the main VLAN to VLAN 4. I noticed this because on the day I decommissioned the old NVR, traffic hitting the router suddenly went from about 5000 kbits/s to 130,000 kbits/s:
Stay in Your VLAN
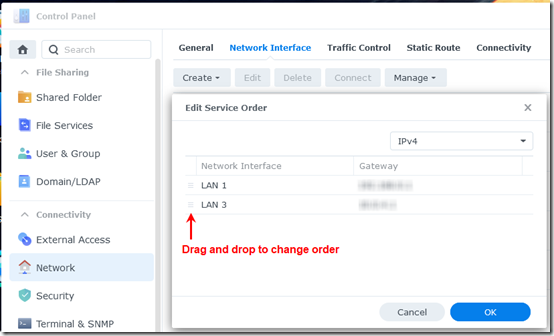
Synology does let you change the order in which it uses NICs:
I tried that on March 3, putting LAN 3 ahead of LAN 1. As you can see above, traffic hitting the router immediately dropped off—it was no longer crossing VLAN boundaries, so it no longer needed to go up to the router. However in this mode, all services on the NAS use the new service order. Unfortunately, there is no way to tell the Synology NAS, “Set Surveillance Station to use LAN 3 only.”
Change the Firewall
The solution turned out to be fairly simple: add a firewall rule to block traffic from LAN 1 on the NAS to the camera VLAN. Conceptually, that means these firewall rules are now:
- New rule: Drop (block) traffic from NAS LAN 1 to all subnets besides the main VLAN.
- Allow traffic from the main LAN to any VLAN.
- Drop (block) all inter-VLAN traffic.
Because rules are interpreted top-down, this means that when the NAS attempts to access the cameras from its first NIC, that traffic goes nowhere. But when it tries from its second NIC, on the same VLAN, that traffic gets through.
Once I implemented the new firewall rule, and set the Synology network service order back to LAN 1 then LAN 3, traffic continued to go directly from the NAS to the cameras without using up router resources.