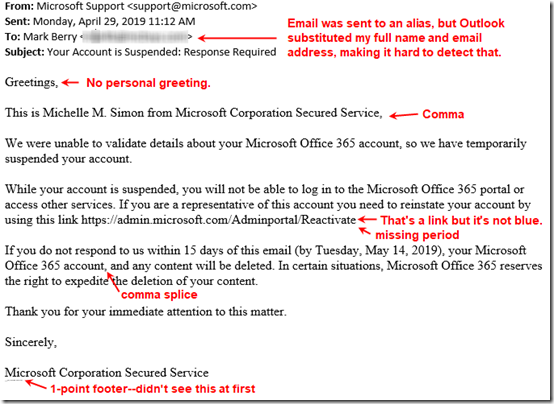
Today, in my Microsoft-hosted email account, I received an email telling me that my Office 365 account needs validation and has been temporarily suspended. I know that’s baloney because I administer that account, but if you are not the admin for your Office 365 account, it might not be so obvious.
The email was well written. I had to really dust off my grammar skills to find a few punctuation errors:
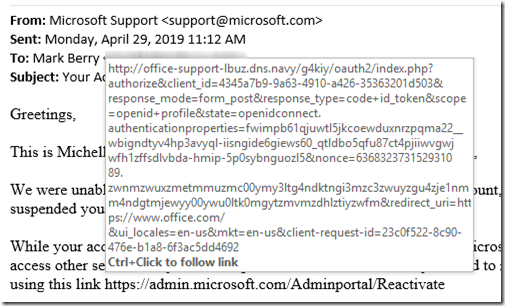
The biggest tell is that the link doesn’t go to where it says it does. By hovering over it (without clicking!), I see that it wants to take me to a dns.navy address. Note that this is NOT a government site; the U.S. Navy would have an address ending in .navy.mil (for military).
A really interesting thing that I haven’t seen before, and didn’t notice at first, is the 1-point footer. After enlarging that font:

I can only assume that adding some text like that helps it to evade spam detection.
Geek Time Out
A couple very technical issues bother me here:
From analyzing the email headers, I see that it was sent to one of my email aliases. However, Outlook (or rather Exchange on the back end) substituted and displayed my primary name and email address. See the top of the first screen shot. That make sit harder to identify as being suspicious.
Office 365 gleefully passed on this phish even though the sender (a machine in Amazon’s east coast did not designate permitted senders. Here’s the source info:
Received-SPF: None (protection.outlook.com:
ec2-18-218-156-163.us-east-2.compute.amazonaws.com does not designate
permitted sender hosts)
Received: from ec2-18-218-156-163.us-east-2.compute.amazonaws.com
(34.196.243.171) by BN3NAM04FT004.mail.protection.outlook.com (10.152.92.98)
with Microsoft SMTP Server id 15.20.1835.13 via Frontend Transport; Mon, 29
Apr 2019 18:25:00 +0000
But wait, in this line, we see CAT:PHSH:
X-Forefront-Antispam-Report:
CIP:34.196.243.171;IPV:NLI;CTRY:US;EFV:NLI;SFV:SPM;SFS:(10001);DIR:INB;SFP:;SCL:5;SRVR:DM6PR13MB2345;H:ec2-18-218-156-163.us-east-2.compute.amazonaws.com;FPR:;SPF:None;LANG:en;CAT:PHSH;
So that means Microsoft knew it was a phishing email but still delivered it to my Inbox!? Why?
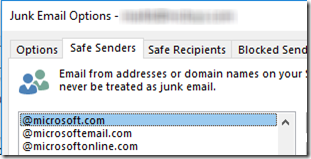
All I can figure is that in spite of the sender being spoofed (support@microsoft), it still applied my “not Junk” exclusion where I designate Microsoft as a safe sender:
Conclusion
Always, always hover over a link before clicking on it.
Check for text in a tiny font.
Consider removing Microsoft (and other often-spoofed companies) from your list of Safe Senders.