I am still pretty early in my journey of learning how to manage Windows 10 Pro updates, but I am a little encouraged to find that there are several setting in Group Policy that are not available in the UI. If it works as expected (and documented), at least with build 1709, you have these capabilities:
- Extend maximum Active Hours from 12 to 18
- Schedule updates e.g. during the night; can even restrict to certain days of the week and/or weeks of the month
- Prevent restarts if a user is logged on
The two key article on this are Build deployment rings for Windows 10 updates and Walkthrough: use Group Policy to configure Windows Update for Business (currently only updated to version 1607).
Manage device restarts after updates has valuable info on group policy settings and the corresponding registry keys for gaining control over restarts.
Even if the machine is not domain-joined, if it’s Pro, you can set these values directly in the registry. Configure Automatic Updates using Registry Editor is a reference of all registry settings.
Group Policy Setup
To see these features in Group Policy Management, you’ll have to install the latest Administrative Templates (.admx) for group policy. The 1709 templates are here.
Loosely following the “Build deployment rings” article above, I decided to create three policies:
- Windows 10 Update – Common Settings (uses WMI to target Windows 10 computers)
- Windows 10 Update – Broad Ring (uses WMI to target Windows 10 computers)
- Windows 10 Update – Fast IT Ring (applies only to my own management computer)
Note If you set your Windows 10 WMI filter to
select * from Win32_OperatingSystem Where Version like '10.%'
it will also include (and apply these policies to) Windows Server 2016. This filter forces it to apply to Windows 10 clients only:
select * from Win32_OperatingSystem Where Version like '10.%' and ProductType='1'
I’ll post my current settings in each policy below.
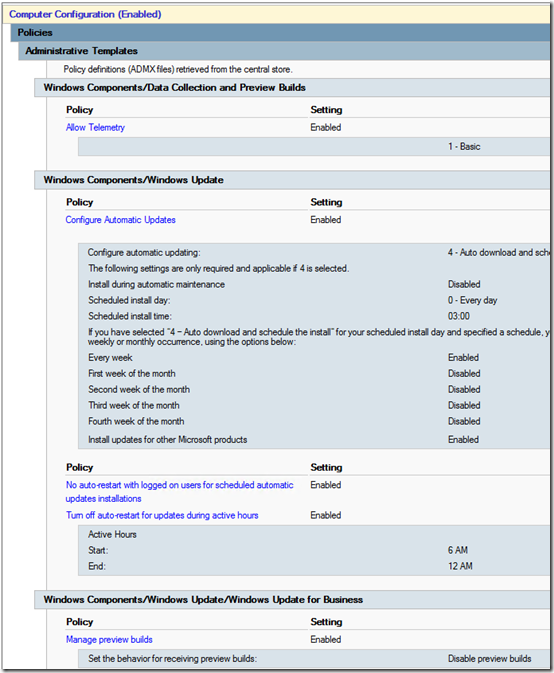
Windows 10 Update – Common Settings
Note that Allow Telemetry must be at least 1 for any of this to work, and Automatic updating must be 4 for scheduled updates to work. I’m doing 3am updates every day, don’t restart if someone is logged on, use an 18-hour Active Hours window of 6am to midnight, and block preview builds.
Update April 9, 2018 4/9/2018 If you use WSUS, under Windows Components > Windows Update, enable “Do not allow update deferral policies to cause scans against Windows Update” per Susan Bradley’s recommendation here. See more info in this TechNet article. The setting has no effect if you’re not using WSUS.
Update May 26, 2020 It turns out that “Turn off auto-restart for updates during active hours” has no effect when “No auto-restart with logged on users” is enabled (see the instructions in the GPO itself). I have now disabled “Turn off auto-restart for updates during active hours.” This allows machines to automatically reboot after installation of updates, as long as no one is logged in. Paired with a script that automatically logs off users each evening, this works pretty well to get Windows 10 machines patched without further intervention.
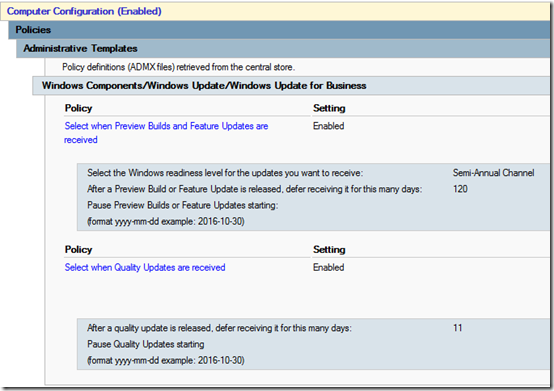
Windows 10 Update – Broad Ring
Yes, 11 days, thinking that if an update comes out on Tuesday, I want it installed on Saturday.
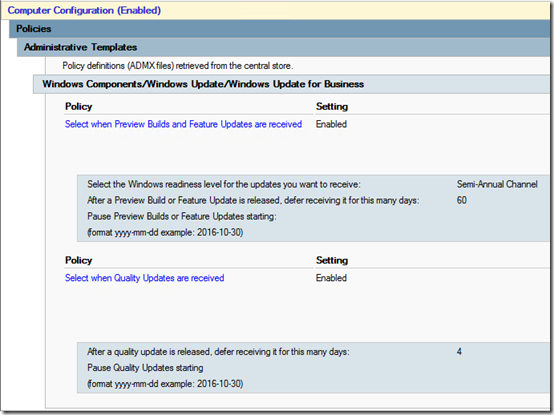
Windows 10 Update – Fast IT Ring
Not dropping to Semi-Annual (Targeted) as recommend by Microsoft; just getting the Semi-Annual Channel after 60 days instead of 120 and quality updates after 4 days.
Client View
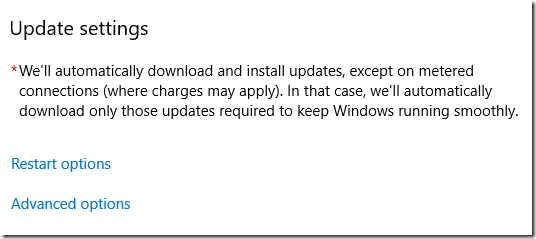
After setting up and applying the policies, it takes awhile (20-30 minutes?) until the Settings app reflects the change. The Active hours option disappears:
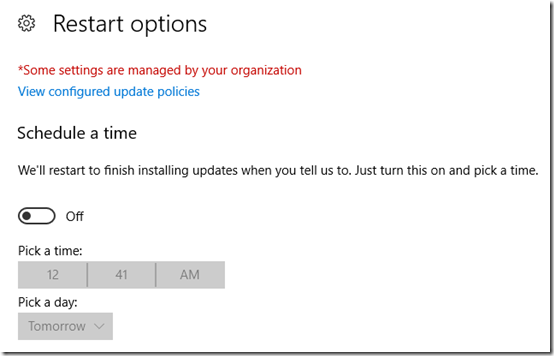
Restart options shows the time, but gives the option to change the schedule:
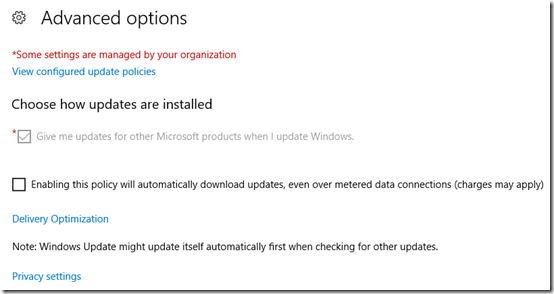
Advanced options was originally showing the 120- and 11-day values, grayed out. Maybe they will return once updates have installed.
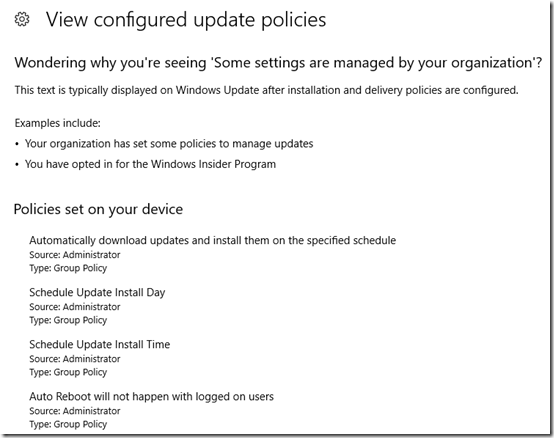
View configured update policies shows what settings are coming from Group Policy, but not what the values are:
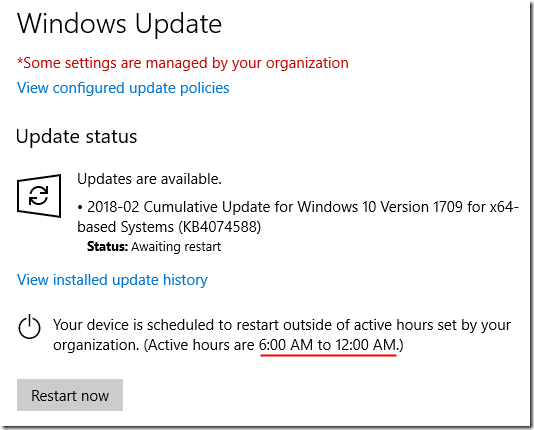
I left my computer logged on last night. It apparently installed updates overnight, but the restart was blocked by policy. I see this now:
Registry values
Most of the settings wind up in HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate and the AU subkey. Here’s what those keys look like in a domain-joined Windows 10 1709 machine (paste to a .reg file if you want to import). This list does not include “Do not allow update deferral policies to cause scans against Windows Update” as it was created for a non-WSUS environment.
Update May 26, 2020 This now shows a Windows 10 1909 machine with the SetActiveHours option disabled. See details above.
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate] "DeferFeatureUpdates"=dword:00000001 "BranchReadinessLevel"=dword:00000020 "DeferFeatureUpdatesPeriodInDays"=dword:00000078 "PauseFeatureUpdatesStartTime"="" "DeferQualityUpdates"=dword:00000001 "DeferQualityUpdatesPeriodInDays"=dword:0000000b "PauseQualityUpdatesStartTime"="" "ManagePreviewBuilds"=dword:00000001 "ManagePreviewBuildsPolicyValue"=dword:00000000 "DisableDualScan"=dword:00000001 "SetActiveHours"=dword:00000000 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU] "NoAutoRebootWithLoggedOnUsers"=dword:00000001 "NoAutoUpdate"=dword:00000000 "AUOptions"=dword:00000004 "ScheduledInstallDay"=dword:00000000 "ScheduledInstallTime"=dword:00000003 "ScheduledInstallEveryWeek"=dword:00000001 "AllowMUUpdateService"=dword:00000001

Mark great article!
I have a question regarding notifications on restarts. how will these notifications work. do i have to set a gpo for warnings and notifications to users on restart times?
thanks
John
@John, sorry I haven’t explored whether notifications can be controlled with group policy.