One of the risks of activating encryption on a hard drive is that you’ll lose the password. It turns out to be pretty simple to save and view BitLocker passwords in Active Directory.
I’m working with Server 2012 R2 Essentials and two Windows 7 laptops.
Turn on Group Policies
With help from this article, I turned on the group policies shown in the graphic below. I included a policy to enable BitLocker without a TPM chip since one of my laptops does not have one. [04/15/2024 – I neglected to link the original source article, but this one from 2020 looks good.] Click on the graphic to expand it in a new window.
Now, when you turn on BitLocker on a domain computer, the keys will be stored in Active Directory.
Enable BitLocker Administration on the Server
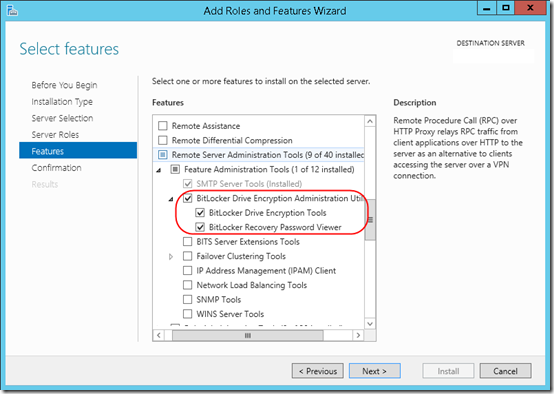
The BitLocker information may be in Active Directory, but you won’t be able to see the information until you add the BitLocker Drive Encryption Administration Utilities feature from the server’s Add Roles and Features Wizard:
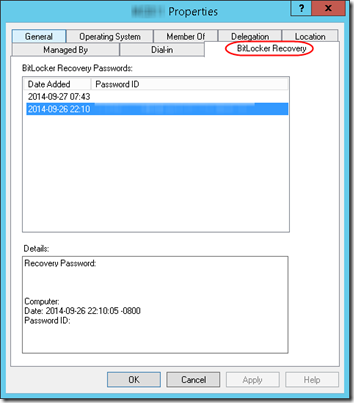
With that set up, go to Active Directory Users and Computers, right-click on a computer, and select Properties. You’ll see a new BitLocker Recovery tab along with a list of recovery passwords (hidden in my screen shot), one for each volume you are protecting with BitLocker:
Note that this doesn’t provide automatic unlocking of the volume; it’s just a backup so you can look up the password in Active Directory if you need it. You should still keep a copy in TPM and on a USB key or other storage. Network unlocking is available under certain circumstances but looks pretty complex; search the web for “BitLocker network unlock”.
Add Keys from Older Computers to Active Directory
If you have computers that were BitLocker-encrypted before you activated the group policies above, their keys will not be added to Active Directory automatically. To add their keys, see this TechNet article [from archive.org; original link]. In short, on the old computer, use manage-bde to key the Numerical Password ID, then use manage-bde again to push the key with that ID to Active Directory:
manage-bde -protectors -get c:
manage-bde -protectors -adbackup c: -id {DFB478E6-8B3F-4DCA-9576-C1905B49C71E}
Check for the password in Active Directory as shown above to confirm it got saved.


An alternative to the standard Bitlocker Recovery Password Viewer is a software called Cobynsoft’s AD Bitlocker Password Audit which features a searchable and filterable gridview overview of all keys which allows you to easily spot machines with missing keys. Using this information paired with your technique above to manually add the keys into the Active Directory using manage-bde you can save yourself some headache down the road if a machine with a missing key were to ask for a Bitlocker recovery key.
http://www.cobynsoft.com/software/cobynsofts-ad-bitlocker-password-audit/
[Editor’s note: Tom’s email address indicates that he works for Cobysoft.]