Years ago, I learned to follow a simple procedure for creating secure passwords:
1. Think of a sentence with at least eight words. Include capital and lowercase letters, numbers, and punctuation.
2. Use the fist character from each word, along with the numbers and punctuation, as the password.
For example, “More people are driving Toyota hybrids 2 work!” becomes “MpadTh2w!”. “Mom spent $20 on groceries @ Vons” becomes “Ms$20og@V”.
How Secure Is That?
Yesterday I came across How to Recover Your Firefox Master Password. Now I use Firefox for most browsing, and a I use the master password feature so that the passwords are encrypted before being stored on disk. I followed the procedure above for creating my master password.
The author of the article was able to use Firemaster‘s brute force approach to recover his 6-character password in 23 minutes. That was because he knew the length of the password and used all lower-case letters.
I wanted to see how long it would take to brute-force my Firefox password. I was willing to tell Firemaster that the password is exactly eight characters long, but I wanted it to use most of the characters on a US English keyboard, including capital letters. So my command line looks like this:
FireMaster.exe -b -m 8 -l 8 -c "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz1234567890`~!@#$%^&*()-_=+[]{}\|,./<>?':;" <path to key3.db>
541,597 Days to Go
After running for about half an hour and trying 265 million passwords, Firemaster is telling me that it has 541,597 days to go. No doubt this would be much longer if it didn’t know the exact password length. I like that.
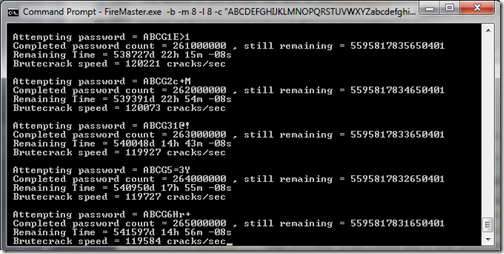
There are undoubtedly faster ways to crack passwords, but I’m glad to see that at least the brute force method seems fairly useless when the password is generated properly.
