I manage several HPE Gen10 Plus v2 MicroServers set up as Hyper-V hosts, running a mixture of Server 2022 and Server 2025. HPE BIOS is currently at v2.40. I discovered a few months ago that although I could enable the Trusted Platform Module for a virtual machine (vTPM), the machine would fail to start.
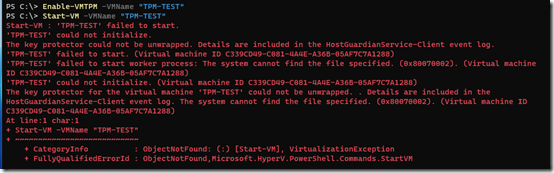
Here is how that looks when trying to start the machine from PowerShell:
Notice the reference to the HostGuardianService-Client event log. There I have these error events:
1025 – “The remote attestation request failed because Isolated User Mode could not be detected.”
2004 – “The Host Guardian Service Client is unable to retrieve the encryption key (IDK) because Virtualization Based Security is not running on this system.”
2014 – “The Host Guardian Service Client failed to unwrap a Key Protector on behalf of a calling process.”
Both the 2004 and 2014 events add this significant line:
”System.IO.FileNotFoundException: Could not find file ‘C:\WINDOWS\system32\config\VSMIDK’.”
System Setup
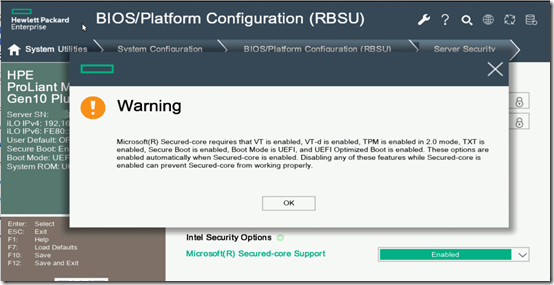
It’s worth noting that I followed the HPE document on Implementing Microsoft Windows Server 2025. In particular, I enabled Microsoft Secured-core support in BIOS:
and I updated the registry to enable virtualization-based security (VBS), Hypervisor Enforced Code Integrity (HVCI), and System Guard:
reg add "HKLM\SYSTEM\CurrentControlSet\Control\DeviceGuard\Scenarios\HypervisorEnforcedCodeIntegrity" /v "Enabled" /t REG_DWORD /d 1 /f
reg add "HKLM\SYSTEM\CurrentControlSet\Control\DeviceGuard\Scenarios\HypervisorEnforcedCodeIntegrity" /v "WasEnabledBy" /t REG_DWORD /d 0 /f
reg add "HKLM\SYSTEM\CurrentControlSet\Control\DeviceGuard\Scenarios\SystemGuard" /v "Enabled" /t REG_DWORD /d 1 /f
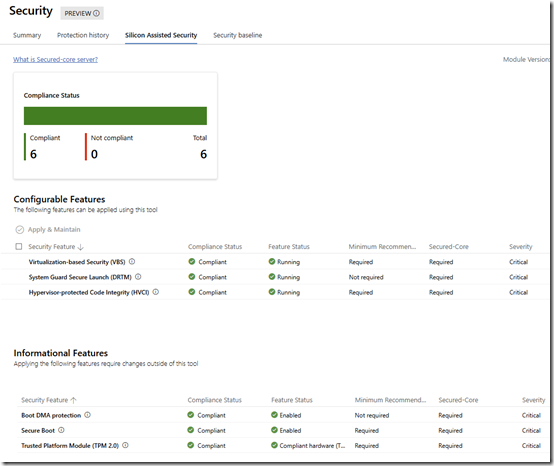
I also checked the values in the Windows Admin Center under Security > Silicon Assisted Security. I had mixed experiences with this, but if the values were not all green, I was able to update them from WAC, reboot, and see them turn green:
Even with those changes, though, the VM would still fail to start and complain about the missing VSMIDK’ file.
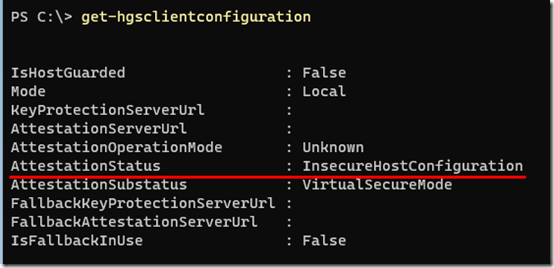
I learned from AI (mostly Google Gemini) that, after installing the Hyper-V role and its utilities, I could run Get-HgsClientConfiguration in PowerShell to check whether the machine was ready to “attest” to Hyper-V so the vTPM could work. As long as it showed AttestationStatus = InsecureHostConfiguration, it would not start a VM with its vTPM enabled:
The Fix
The fix was suggested four years ago in this reddit thread—clearing the TPM:
Sure enough, after clearing the host TPM (see cautions below) and rebooting, the VSMIDK file was automatically created at boot, AttestationStatus changed to “Passed”, and I was able to start a VM with a vTPM without error: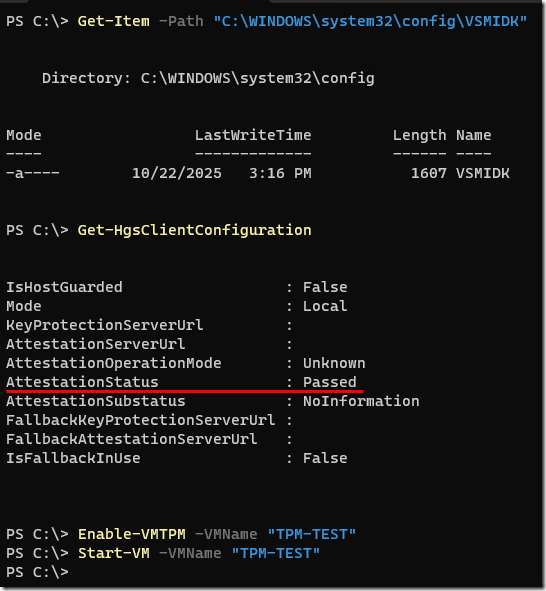
Careful with TPM Reset – Step by Step
Clearing the TPM will delete any BitLocker keys you have stored there, so be sure to save/print your BitLocker keys before you clear the TPM! Apparently you can store other stuff like certificates in the TPM. I guess I wasn’t doing that, but proceed here at your own risk. On the host machine:
1. Check if the VSMIDK file exists. If it does, stop—you have a different issue and these steps aren’t for you.Get-Item -Path "C:\WINDOWS\system32\config\VSMIDK"
2. Go to Manage BitLocker and Back up your recovery key. Or use PowerShell to view and save the key(s):(Get-BitLockerVolume -MountPoint "C:").KeyProtector
3. From Manage BitLocker, choose Suspend protection.
4. Run tpm.msc. In the right-hand Actions column, choose Clear TPM…
5. Reboot. This will automatically re-enable BitLocker protection.
6. Check if the VSMIDK file was created and if AttestationStatus has changed:Get-Item -Path "C:\WINDOWS\system32\config\VSMIDK"
Get-HgsClientConfiguration
If the file is there and AttestationStatus = Passed, you should be able to start a VM with a vTPM.
7. Make sure you have your BitLocker keys ready and reboot again. You’ll be prompted to enter the key for drive C: on boot. Subsequent reboots should pull the key from the TPM.
What Happened?
It’s unclear why Windows Server—on several different HPE MicroServers—was unable to create the VSMIDK file on boot even with Secured Core features fully enabled. AI suggested that BitLocker sealed the TPM so it could not be accessed or updated for creating the VSMIDK file. I do use BitLocker on all servers, but I’m pretty sure I encrypted the drives after enabling Secured Core stuff, so why wasn’t the VSMIDK file created first? And why wouldn’t Windows or the BIOS be able to unlock the TPM to create the VSMIDK even if BitLocker is running?
I don’t really understand all the inner workings of the TPM, VBS, HVCI, and System Guard, whether it’s the OS or the BIOS or some handshake between them that was blocking creation of that critical file. I’m just glad that the step-by-step TPM reset allowed me to get vTPMs working and that BitLocker also still works as usual.