I wrote recently about setting up guest wireless with the Tomato router firmware. I also needed to be able to use site-to-site OpenVPN between two routers running Tomato. I’m using a “Toastman” build that includes both VLAN and VPN functionality, but how can I use them at the same time?
This is the main article I followed for setting up a site-to-site VPN:
It seems that the last bit of his step 3, where you add 1194 to the port forwarding, is no longer required.
VPN Can’t Ping from LAN to LAN
Unfortunately after configuring the VPN, I could ping from the router to the other LAN, but I could not ping from one LAN to the other LAN. Not good!
I got lots of help from the VPN and VLAN and authors. Long story short: the VLAN setup was not allowing packets on the local LAN to be forwarded to the VPN tunnel.
The solution is to manually add a one-line forwarding instruction to each router. The exact instruction depends on which VLAN you wan to route to which VPN tunnel.
The VLANs are listed under Advanced > VLAN. Choose the Bridge name for the VLAN you want to connect. 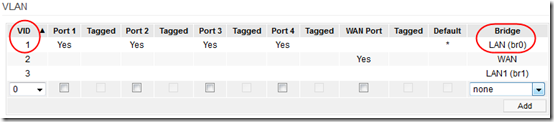
The tunnels are named as follows: tun11 = OpenVPN Client1, tun12 = Client2, tun21 = Server1, and tun22 = Server2. You can see which tunnel is active under Advanced > Routing. This screen shot is from my OpenVPN server: 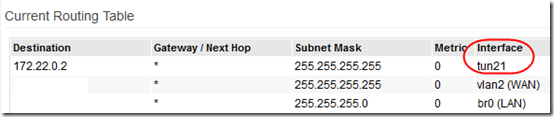
On both the client and sever, my main LAN (that I want to share across the VPN) is on br0. The server is tun21 and the client is tun11. So on the OpenVPN server router, I ran this instruction from Tools > System:
iptables -A FORWARD -i br0 -o tun21 -j ACCEPT
and on the OpenVPN client router I ran this instruction:
iptables -A FORWARD -i br0 -o tun11 -j ACCEPT
Voila! Bi-directional ping happiness, from server’s LAN to client’s LAN and vice-versa.
To make the instructions “sticky,” save the corresponding instruction in Administration > Scripts > Firewall on each router, and reboot the router.
This functionality may eventually become “standard” or part of the GUI, but for now, a pair of simple instructions lets you use OpenVPN on a router running VLANs.

Pingback: Set Up Guest Wireless with Tomato | MCB Systems
Hello Mr Berry.
Have you tried this on the latest versions of tomatousb? Formerly this worked allright using your instructions, which meant adding the firewall script basically.
Just purchased another router (asus rt-16n) and updated to software on both routers that talk to each other and for some reason it does not work anymore. The openvpn server router is the asus running shibby 083v and the openvpn client router is a netgear 3500l running v1.28.4494 MIPSR2-Toastman-VLAN-RT K26 USB VPN-NOCAT
I am able to ping the each of the router from the other router. I am also ablo to ping the router from any of the lan clients (both from the openvpn server side and the openvpn client side). However, I cannot ping a client of a lan from another client of the other lan in either direction.
Reading the forums, it is (somewhat) indicated that Teaman might have addressed this so you don’t need the firewall extra config scripts? Do you know anything about that? Does it still work for you and are you using the latest versions of tomatousb?
Henrik,
Should have put this in the article:
VPN server is Linksys E2000 with v1.28.4407 MIPSR2-Toastman-VLAN-RT K26 VPN
VPN client is Linksys E3000 with v1.28.4407 MIPSR2-Toastman-VLAN-RT K26 USB VPN
Yes it’s still working and no I haven’t updated firmware since then. You might try adding to the thread I started, or starting another on the same forum:
http://www.linksysinfo.org/index.php?threads/site-to-site-vpn-can-ping-from-router-but-not-from-inside-network.35804/
I am having a similar problem as Henrik with tomato-ND-1.28.7632.1-Toastman-VLAN-IPT-ND-VPN on a WRT54GL
I am having trouble with this also. I have two identical Netgear WNR3500L/U/v2 routers, each
running Tomato Firmware v1.28.7494 MIPSR2-Toastman-VLAN-RT K26 USB VPN-NOCAT
One is set up as a OpenVPN client at my home, and the other is set up as a OpenVPN server at my office.
I would like to link my two LAN’s together. Home LAN is 192.168.0.x and Office LAN is 64.72.146.x
I know the 64.72.146.x is weird, but I have hard wired software licenses on that network that I do not want to replace. This was once a real network of mine, but I changed providers and now just treat it like a 192. network.
Currently I can ping from my home (client) LAN to the Office (server) LAN, but not the other way around.
I got hung up when I tried to put in my home network 192.168.0.0 netmast 255.255.255.0 push
in my OpenVPN server1 advanced screen. With this in there, I would fire up my OpenVPN client on my home router and it would hang up to the point where I would have to 30-30-30 reset the whole router and restore configuration. I finally got smart and turned off the “Start with WAN” in the basic screen so all I would have to do is reboot the router and disable the PUSH setting.
I am thinking about setting both routers up as a client and server for OpenVPN so they will join the Lan’s on each side but that does not seem like a elegant solution.
Please let me know what I should try next.
Tom, I’m glad to have your query here, but you might reach a broader and more qualified audience by posting it at the LInksysinfo Tomato forum: http://www.linksysinfo.org/index.php?forums/tomato-firmware.33/.
If Tom doesn’t manage to find the appropriate OpenVPN discussion in that forum I’ll post my experiences here for reference…
As far as I know, the toastman version you are using have not received the latest updates from Teaman, which basically means you have to follow Mr Berrys advice regarding putting extra rules in the firewall script (somewhere on the administration page)
The weird lans should work as long as it not a public ip that someone else could have. (That is my opinion at least, ymmv)
In some setups the client network will completely disappear if you have the wrong settings, for me that was the case at least. I was locked out from all Internet access on the client when it tried to connect to an OpenVPN server using the wrong settings.
Use start with wan only when you know it works, no need to activate it the first time you try.
The settings I have checked on my server advanced are:
Push LAN to clients [checked]
Manage Client-Specific Options [checked]
Allow ClientClient [checked]
Allow Only These Clients [checked]
[checked] client 192.168.201.0 255.255.255.0 [checked]
The rest on that page is either not checked, 0 or -1. (The defaults basically)
I had the same thoughts before, settings up each side as both server and client, but I have since put those thoughts to rest. With the settings I’ve outlined above, and the extra firewall settings Mr Berry has provided it now works site to site from both sides (client and server). If you use Shibby firmware, it seems like he has updated the code to automatically adjust for the extra things Mr Berrys suggests in the above post, at least I am able to ping clients of that lan without adding specific rules to the firewall..
And Mr Berry, if you know the link to the actual OpenVPN discussion, I could benefit from that too. Perhaps it is indeed the one you gave me: http://www.linksysinfo.org/index.php?threads/site-to-site-vpn-can-ping-from-router-but-not-from-inside-network.35804/
Cheers! =)
Thanks. I think I will first follow Toastman’s advice and completely 30-30-30 reset both routers and set them both up manually rather than restoring configuration files. I’ve been flash happy trying different toastman builds. I did not realise that you should not restore a configuration from a different build and probably screwed something up by trying to save time and effort.
I’ll check out the forum you mentioned.
Thanks Henrik. Yes, that link (http://www.linksysinfo.org/index.php?threads/site-to-site-vpn-can-ping-from-router-but-not-from-inside-network.35804/) is to a thread I posted where I got some help from the author of the VPN add-on (SgtPepperKSU). That thread links to this one:
http://www.linksysinfo.org/index.php?threads/vlan-tags-work-for-you.34478/page-5#post-174323
where the VLAN author, teaman, pointed me to this thread about adding iptables entries:
http://www.linksysinfo.org/index.php?threads/tomato-raf-with-included-bittorrent-client-beta-testing.33858/page-16#post-171514
I think I should point out that my article above is only designed to help if you use VLAN *and* VPN together. If you’re not using VLANs, it shouldn’t be necessary. If you *are* using both, regarding the additional tunnels, SgtPepperKSU says in the first thread, “Since it will be harmless (though, unnecessary) in the non-VLAN case, I’ll add it to TomatoVPN code. So, it’s likely that in the future you won’t need those rules in your firewall script.” I take this to mean that if you have a later version than what I used (see my 1/21 comment), even if you are doing both, you should no longer need to add the iptables commands.
My head is hurting…. Probably because I was playing with this till 3:00 am.
Anyone care to take a peek and see. This network is experimental and not the real project they want me to work on.
Server Router is at [deleted]
Home Router is at [deleted]
I’ll make the admin password on both “helpme” for a while.
If you break it, no big deal. I have pre-configured spare routers I can swap out.
Tom
Tom, never do what you just did!
Anyway, it should now work. I am able to ping each server from the other server.
Whoever is in there, it is pinging both ways now!
Henrik,
Please tell me what you did to get it working.
Tom, sounds like you got the help you needed so I’m deleting your IP info above. Do I need to give you guys each other’s email addresses? Feels like a dating service ;). Actually Henrik I imagine you could reach Tom through his company–just click on his name to get to his web site.
I fell somewhat inappropriate spamming Mr Berrys site with this, but hey, he can always delete it later =)
I made sure that these settings were in effect (like described in my earlier post):
Push LAN to clients [checked]
Manage Client-Specific Options [checked]
Allow ClientClient [checked]
Allow Only These Clients [checked]
[checked] your_common_name 192.168.X.X 255.255.255.0 [checked]
In the last setting you had the CN (common name) set to HomeLan, but in reality the CN was mooresville or something like that… So I changed it and that was all that was needed.
To my knowledge, if you haven’t specifically named your clients, the settings won’t be properly pushed. Not sure if that is a defect or a security measure though.
I did not try pinging any of the clients of any of the lans. Perhaps you need the extra config Mr Berry mentioned in the first post for that.
Henrik,
Thanks, I believe that was my mistake getting the common name wrong (should have been mooresville and not homelan. Pesky Common Names! Everything is pinging now. Thanks for all your help. I thought the problem was something much more complex but as you pointed out, it was something simple and right under my nose.
I’m pretty confused on this whole thing…I’ve set it up as per the same instructions you followed, I haven’t setup any VLANS is that necessary? I can see the other router under status but I can’t ping anything.
Justin – if you’re not using VLANs, you shouldn’t need the adjustments described in this article.
I didn’t think so. I can’t ping anything on the server side tho, any suggestions.
Oh also remote desktop works…Just can’t ping.
Justin, maybe the firewall on the remote server is not allowing ping (icmp) from remote networks.
Makes sense….Thanks Mark
I am assuming you are using TUN and not TAP.
Any suggestions on how to get TAP working? I have the same issue where I can not ping computers on the other wide.
Tom – yes, using TUN. Sorry, no experience with TAP.
can you please look at this link? and help me. thanks
sorry this link
http://www.linksysinfo.org/index.php?threads/tomato-client-cannot-access-computers-behind-vpn-server.37190/#post-181266
Replied here:
http://www.linksysinfo.org/index.php?threads/tomato-client-cannot-access-computers-behind-vpn-server.37190/#post-181301
Hi Mark,
Greetings from Singapore. I am totally new to this stuff. I am more of a “plug and play” person. I would like to configure the router to leverage StrongVPN PPTP service in US for my media devices only and not the entire clients at my place. What’s the easiest way to do this ? Thanks
Charmaine – Tomato is definitely not “plug and play”! You might be able to set up some kind of subnet for specific devices but I’m afraid I don’t know how. You could try asking on the Linksys Tomato forum: http://www.linksysinfo.org/index.php?forums/tomato-firmware.33/.