Today I visited www.dmachoice.org, the web site of the Direct Marketing Association, intending to update my opt-out preferences. I was surprised when one of the pages took me off their site to a third-party page. When it happened a second time, I started looking for signs that the site had been hacked.
Clue #1: Random Redirects
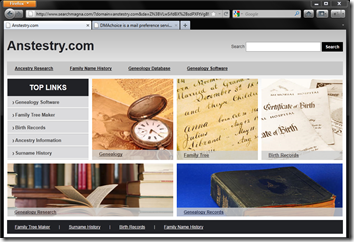
Every so often while browsing the site, I wind up on another site. The site I was referred to was designed to look like a legitimate web page, but it’s actually a search page. For example, this site below might at first glance appear to be ancestry.com, but it’s spelled an-test-ry, and the URL at the top actually comes from searchmagna.com:
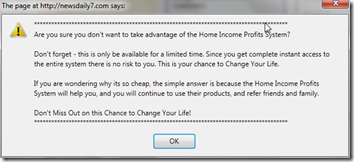
At one point, even though the main dmachoice.org site was displayed, I got a pop-up asking if I really wanted to leave a Home Income Profits site:
This led to other popups, which I know can lead to virus downloads, so I went to Task Manager and killed firefox.exe.
Clue #2: Loading Data from Third-Party Sites
I started watching where dmachoice.org was pulling data from as the page loaded. Here you see a live capture of the Firefox status area site as it accesses sites like js.users.51.la, www.searchnut.com, 205.209.161.4, etc.:
Sometimes I saw references to sites for legitimate businesses (like thrifty.com and 1800flowers.com) that have no business on the dmachoice.org site.
Clue #3: Check Sources of Media on Page
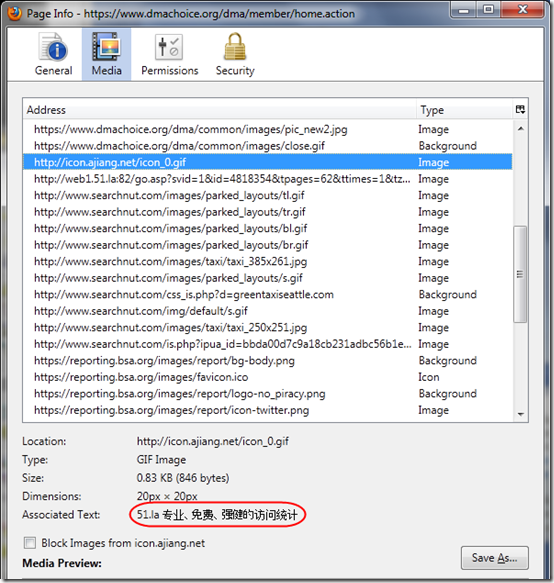
Firefox has a very useful feature that lets you review all the sources of media on a page. Right-click on the page and select View Page Info. You’ll see a dialog like this:
Scrolling down the list of media, after several legitimate images from the dmachoice.org site, there are lots of additional images from sites like ajiang.net, 51.la, and searchnut.com. With help from Whois lookups at www.iptools.com, we can see that the first two are registered in China and the last in Grand Cayman. Note the “Associated Text” from icon.ajiang.net is an Asian script, and references 51.la, the next site loaded.
SSL is Not Enough
It’s worth noting that although the main dmachoice.org site is SSL-encrypted (begins with https://), it still pulls data from non-secure sites.
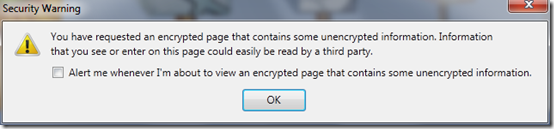
To its credit, Internet Explorer 8 asks before loading unencrypted data and gives you the option to suppress it:
If you accept the default answer (“Yes”), IE does not load data from the third-party sites. (If those sites were also https:// sites, it might still load them.)
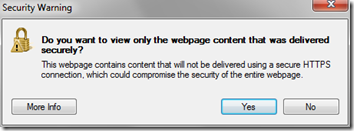
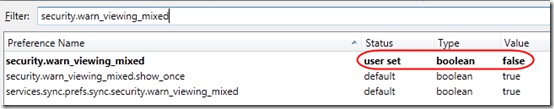
Firefox also warns about mixed content by default, but it only warns once, and it does not give the option of suppressing the non-secure content. If you accept the defaults of this warning, you’ll immediately start downloading the extra content, and you’ll never see the warning again:
In Firefox 4, the only way to re-enable the warning is through an advanced about:config process (see Firefox question 826495). Here is what it looks like after clicking OK on the warning:
Why the Hack?
So why has the site been hacked? What are the hackers gaining from it? My guess is that they are paid for referrals. By hijacking a busy site and forcing users to jump to other sites (or maybe just by referencing the other sites), they get advertising revenue.
Of course if they have full access to the site, they could also be harvesting user names and passwords as users log in, or potentially download the entire DMA database. Since the DMA is the main association used by consumers to set postal mail preferences, their database is no doubt quite large. The hackers could also set up the site to download viruses to user computers in addition to referring visitors to other sites.
I contacted the DMA by email and phone before writing this article but have so far not heard a response.

interesting
For anyone landing on this travesty of an article. The author has malware on his computer, it’s not a hacked website.
“Me”, thanks for sharing your opinion. Sometimes it is malware on the computer, but then I would have been seeing browser hijack behavior on multiple sites, not just one. In this case, it was the site itself. Fortunately, dmachoice.org seems to have fixed the problem sometime in the last 3.5 years.
[removed URL of potentially hacked web site]
Thinking that I found an extremely helpful website, they took control of my Google Acer notebook. Eeeghads! Fortunately re-booting eliminated the problem, but what if it didn’t and why wouldn’t it let me just close it? Aren’t there laws to prevent this?
This is after a boiler room hacking operation failed to gain entre into an account of mine. They actually called my home phone 10x, misrepresenting themselves as Dell operatives. Initially asking if I had problems with my Dell laptop, specifically one of my Gmail accounts. Even if I hadn’t touched that unit for months, I was floored. After 49 minutes I managed to record several minutes, while only contacting a tech rep with Dell. Another waste of time. Curiosity got the worst of me.
Is there a way to shut these creeps down?
Many thanks,
Stan Shaffer